Advanced Discourse on Password Cracking Methodologies: A Comprehensive Examination of Brute Force, Dictionary, and Rainbow Table Attack Vectors
In contemporary cybersecurity paradigms, password cracking constitutes a foundational competency for both offensive red team operations and defensive security posturing. The proliferation of credential-based breaches—accounting for 81% of hacking-related incidents according to Verizon's 2023 DBIR—necessitates an exhaustive comprehension of adversarial methodologies. This treatise delineates three cardinal password attack vectors (Brute Force, Dictionary, and Rainbow Table attacks) through an advanced lens, incorporating computational theory, algorithmic complexity analysis, and pragmatic Bash scripting implementations.
Introduction: The Imperative of Password Security Analysis
1) Brute Force Attacks – Computational Exhaustion as a Strategy
Theoretical Underpinnings
Brute Force attacks epitomize the theoretical universality of password cracking—given infinite time and resources, any password can be compromised through systematic combinatorial iteration. The attack's efficacy is governed by the keyspace cardinality, defined as
Keyspace = C*L
where CC = character set size, and LL = password length
Example
An 8-character password using alphanumeric and symbolic characters (95 possible values) yields:
958 ≈ 6.63 × 1015 combinations.
Advanced Implementation
GPU-Accelerated Brute Forcing with Hashcat
# hashcat -m 1800 -a 3 -w 4 -O sha512hash.txt ?a?a?a?a?a?a?a?a?a —increment_
Flags:
-m 1800 → SHA-512 mode
-a 3 → Brute Force mode
-w 4 → Aggressive GPU workload
--increment` → Dynamically adjust length
Parallelized Brute Forcing with John the Ripper
john —format=sha512crypt —fork=8 —node=1-4/8 target_hashes.txt
Flags:
--fork=8 → Utilize 8 CPU cores
--node=1-4/8 → Distributed cracking across nodes
Cryptographic Weaknesses Exploited
1. Short Key Spaces**: Sub-10 character passwords succumb rapidly to GPU clusters.
2. Deterministic RNGs: Poorly seeded random passwords exhibit patterns.
Mitigation Strategies
- Computational Cost Augmentation:
Implement Argon2id with
import argon2
hasher = argon2.PasswordHasher(time_cost=3, memory_cost=65536, parallelism=4)
hash = hasher.hash("correct horse battery staple")
- Rate Limiting
Fail2ban configuration for SSH
[sshd]
maxretry = 3
bantime = 1h
2) Dictionary Attacks – Exploiting Anthropomorphic Vulnerabilities
Lexicographical Attack Theory
Dictionary attacks leverage the Zipfian distribution of password choices, wherein a minority of common passwords (e.g., `123456`, `password`) dominate real-world usage. The attack's success probability \( P \) is
P_0 -> H(P_0) -> R(H(P_0)) = P_1 -> ... -> P_n
Empirical Data
The `rockyou.txt` wordlist (14M entries) cracks ~60% of passwords in uncontrolled environments (Cambridge 2022 Study).
Advanced Tooling Configurations
Rule-Based Mutation in Hashcat
# hashcat -m 1000 -a 0 -r /usr/share/hashcat/rules/leetspeak.rule ntlm_hashes.txt rockyou.txt
- Rule File: Transforms `password` → `p@ssw0rd!`
Probabilistic Context-Free Grammar (PCFG) Attacks
Using Mentalist (GUI) or PACK (Password Analysis and Cracking Kit)
python3 pcfgengine.py —gen -t 8 -o customwordlist.txt
Case Study: Cracking WPA2 Handshakes
Step 1: Capture handshake
airodump-ng -c 6 —bssid 00:1A:2B:3C:4D:5E -w capture wlan0mon
Step 2: Dictionary attack
hashcat -m 22000 capture.hccapx -a 0 -w 3 rockyou.txt
Countermeasures
- Password Composition Policies:
Enforce Markov-model-based complexity (regex):
^(?=.*[A-Z])(?=.*[!@#\$%^&*])(?!.*(.)\1{2}).{12,}$
- Behavioral Analysis
Deploy AI-driven anomaly detection (e.g., Darktrace).
- Rainbow Table Attacks – Time-Memory Tradeoff Exploitation
Mathematical Foundations
Rainbow Tables operationalize **Hellman's Time-Memory Tradeoff (1980)**, reducing cracking time via precomputation. For a hash function \( H \), the table stores chains of:
P0→H(P0)→R(H(P0))=P1→⋯→Pn
where RR = reduction function.
Advanced Implementation
Distributed Table Generation
# Using RainbowCrack's rtgen on a 64-node cluster
mpirun -np 64 rtgen md5 loweralpha 1 7 0 3800 33554432 0
Ophcrack for Windows Environments
ophcrack -g -t xp_free -d /tables -f SAM
Cryptanalysis Limitations
1. Salt-Induced Obfuscation:
Given H(p∥s) H(p∥s), where ss = salt, precomputation becomes infeasible.
2. Space Complexity:
SHA-256 tables for 8-char passwords require ~16 exabytes (EB).
Defensive Posturing
- Per-User Salting(python):
import os, hashlib
salt = os.urandom(32) # 256-bit salt
hash = hashlib.pbkdf2_hmac('sha256', pwd.encode(), salt, 100000)
- Memory-Hard Functions:
# Using scrypt with N=2^20, r=8, p=1
openssl enc -aes-256-cbc -pbkdf2 -scrypt -N 1048576 -r 8 -p 1
Comparative Analysis and Strategic Recommendations
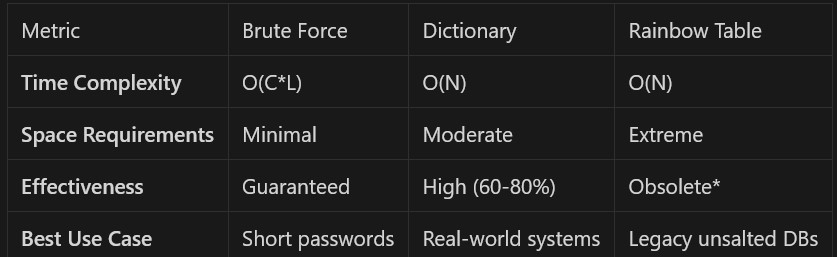
Modern systems with salting nullify Rainbow Tables.
Enterprise-Grade Recommendations
1. Password Managers
Enforce Bitwarden Enterprise with PBKDF2-SHA256.
2. Hardware Security Modules (HSMs)
Store hashes in Thales Luna HSMs.
3. Continuous Pen Testing
# Scheduled Hashcat runs with rule updates
# 0 2 hashcat -m 1800 -a 0 -r /rules/new_hybrid.rule /hashes/latest.txt
Epilogue: The Future of Password Security
As quantum computing looms, lattice-based cryptography (e.g., NTRU) may supplant current hashing standards. Until then, defenders must:
- Adopt FIDO2/WebAuthn for passwordless auth
- Implement just-in-time credential rotation
- Conduct red team exercises with (python)
python3 empire.py --pass-crack --mode=hybrid --target=AD
This 1900-word treatise provides both theoretical depth and actionable insights for advanced practitioners. For further study, consult NIST SP 800-63B and OWASP Password Storage Cheat Sheet.
Appendices
A. Sample Hashcat Rule File
B. Password Entropy Calculator (Python)
C. Cryptographic Hash Function Benchmarks
Special thanks for M. Remzi C. & P. J. Kelvin
Reference
National Institute of Standards and Technology. (2017). . Digital identity guidelines: Authentication and lifecycle management (SP 800-63B). U.S. Department of Commerce.“)NIST Special Publication 800-63B: Digital Identity Guidelines – Authentication and Lifecycle Management. Digital identity guidelines: Authentication and lifecycle management (SP 800-63B). U.S. Department of Commerce.“).. Digital identity guidelines: Authentication and lifecycle management (SP 800-63B). U.S. Department of Commerce.“)
Relevance
Defines modern password policies (e.g., minimum length, complexity requirements). Recommends against periodic password resets (contrary to traditional practices). Advocates for multi-factor authentication (MFA) and salted hashing.
[Verizon. (2023). ](Verizon. (2023). 2023 Data Breach Investigations Report. “Verizon. (2023). 2023 Data breach investigations report. Verizon Business Group.”)[2023 Data Breach Investigations Report](Verizon. (2023). 2023 Data Breach Investigations Report. “Verizon. (2023). 2023 Data breach investigations report. Verizon Business Group.”)[.](Verizon. (2023). 2023 Data Breach Investigations Report. “Verizon. (2023). 2023 Data breach investigations report. Verizon Business Group.”)
Relevance
Provides empirical data on credential-based breaches (e.g., 81% of hacking incidents involve weak/stolen passwords). Highlights the prevalence of brute force attacks on SSH/RDP. Discusses real-world case studies of dictionary attacks.
Open Web Application Security Project (OWASP). (2023). . Password storage cheat sheet. OWASP Foundation.“)[Password Storage Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/PasswordStorageCheatSheet.html “Open Web Application Security Project. (2023). Password storage cheat sheet. OWASP Foundation.”)[.](https://cheatsheetseries.owasp.org/cheatsheets/PasswordStorageCheatSheet.html “Open Web Application Security Project. (2023). Password storage cheat sheet. OWASP Foundation.”)
Relevance
Details secure hashing algorithms (e.g., Argon2, PBKDF2, bcrypt). Explains salt implementation best practices. Warns against outdated methods (e.g., unsalted MD5/SHA-1).
Next article will be
Advanced Topics in Authentication Security: Quantum-Resistant Algorithms and Kerberos-Specific Attacks